只要有電腦和網絡,就會有網路事件。而SOC的有效性取決於其應對方式和時間。
As long as there have been computers and networks, there have been cyber
incidents. Typically, a SOC’s effectiveness is determined by how and when it responds.
Responding to incidents is at the core of the SOC
incident handling is considered a broader term than incident response, suggesting it encompasses tracking and reporting
這領域很深,以下是書上建議閱讀清單
Computer Security Handling Guide (800-61)
https://csrc.nist.gov/pubs/sp/800/61/r2/final
Guide for Cybersecurity Event Recovery (800-184)
https://csrc.nist.gov/pubs/sp/800/184/final
Recovering from a Cyber Security Incident
https://www.nist.gov/system/files/documents/2017/12/01/recovery-webinar.pdf
VERIS: The Vocabulary for Event Recording and Incident Sharing
http://veriscommunity.net/index.html
ENISA: Reference Incident Classification Taxonomy
https://www.enisa.europa.eu/publications/reference-incident-classification-taxonomy
MISP Taxonomies and Classification as Machine Tags
https://www.misp-project.org/taxonomies.html
The Cyber OODA Loop: How Your Attacker Should Help You Design Your Defense
https://csrc.nist.gov/Presentations/2015/The-Cyber-OODA-Loop-How-Your-Attacker-Should-Help
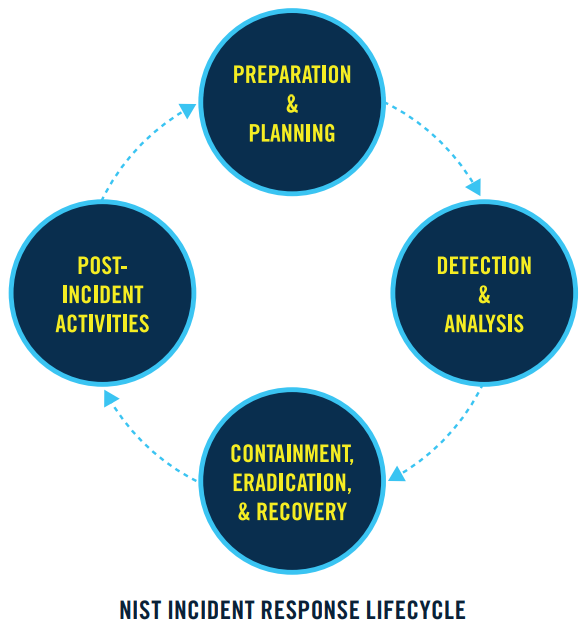
為了確保有效率的處理事件,需要制定好相關的計畫
每個行業有不同定義,書上舉AT&T對於DDos優先權大於未經授權驗證(跟表格上不同,不知道是不是書本筆誤...)
透過定義事件類別、回應步驟和級別升級程序,列入標準作業程序(SOP),為處理事件做好準備
確立組織對於事件的優先順序並分配回應資源
「優先處理事件應對」而非僅僅執行事件應對
is named prioritize incident response as opposed to do incident response
AT&T 優先級別表格以及ATT&CK參考
| 分類 | 優先級別 | 回應處理 |
|---|---|---|
| port Scanning(事前) | Low | 忽略,已知不良信譽的加入阻擋 |
| Malware infection | Medium | 修復並掃描同一區域避免擴散 |
| Denial of service | Low-Medium | 依持續時間逐步增加,與ISP協調 |
| Unauthorized access | High | 重建帳戶、系統修復 |
| Insider threat | High | 關閉訪問 |
| Web attacks | High | 調查事件的範圍 |
| Phishing | Medium | 檢查是否有其他收件者 |
| Lost or stolen device,ransomware | Low-High | 依資料的敏感性 |
| Poor security practices observed | Low-Medium | 合規性處理 |
Team members must be given enough structure to ensure that expectations such as consistency, timeliness, and the removal of analytic bias are met, while also being given the freedom to act on their intuition and experienc
committed entirely to one person's memory and only that person's memory, you've got to get it written down
分類可以幫助將潛在的緊急情況與常規事件需求區分開來
Triage helps coordinators or analysts separate out potential emergencies from routine response needs.
每個攻擊事件都是獨一無二的,要確保處理回應合乎事件
Each attacker-based incident is unique, it is important to ensure the response fits the incident
大多數的事件都沒偵測到最初得進入點 (程式碼比較少、或使用正常的工具,行為較隱密),因此不能只看告警訊息,而是要一步步追查,這需要大量資料(Log)以及工具,EDR是近期因此興起的工具。
Most incidents are not detected at the initial entry point.
True and False Positives and Negatives
持續調整、完整上下文(Log關聯)和自動化更有效率地理解真正有價值的訊息
False positives outnumber true positives in most detection systems. Continual tuning, strong context enrichment, and automation are critical to understand effectively and efficiently what is truly of value.
因資源有限,需依優先順序處理事情,而優先的方法要定義出來提供成員參考,而定義的類別可以參考MITRE ATT&CK,最後要指派一個人負責與長官或其他單位溝通,讓事件處理人員專心,避免被打斷
Strategy 5: Prioritize Incident Response
